Securing the Perimeter: Navigating Edge Computing Security Challenges
As businesses embrace the decentralized architecture of edge computing, the critical importance of robust security measures cannot be overstated. This article delves into the intricacies of edge computing security, examining the challenges, strategies, and the evolving landscape of safeguarding data at the edge.
Understanding Edge Computing’s Unique Security Landscape
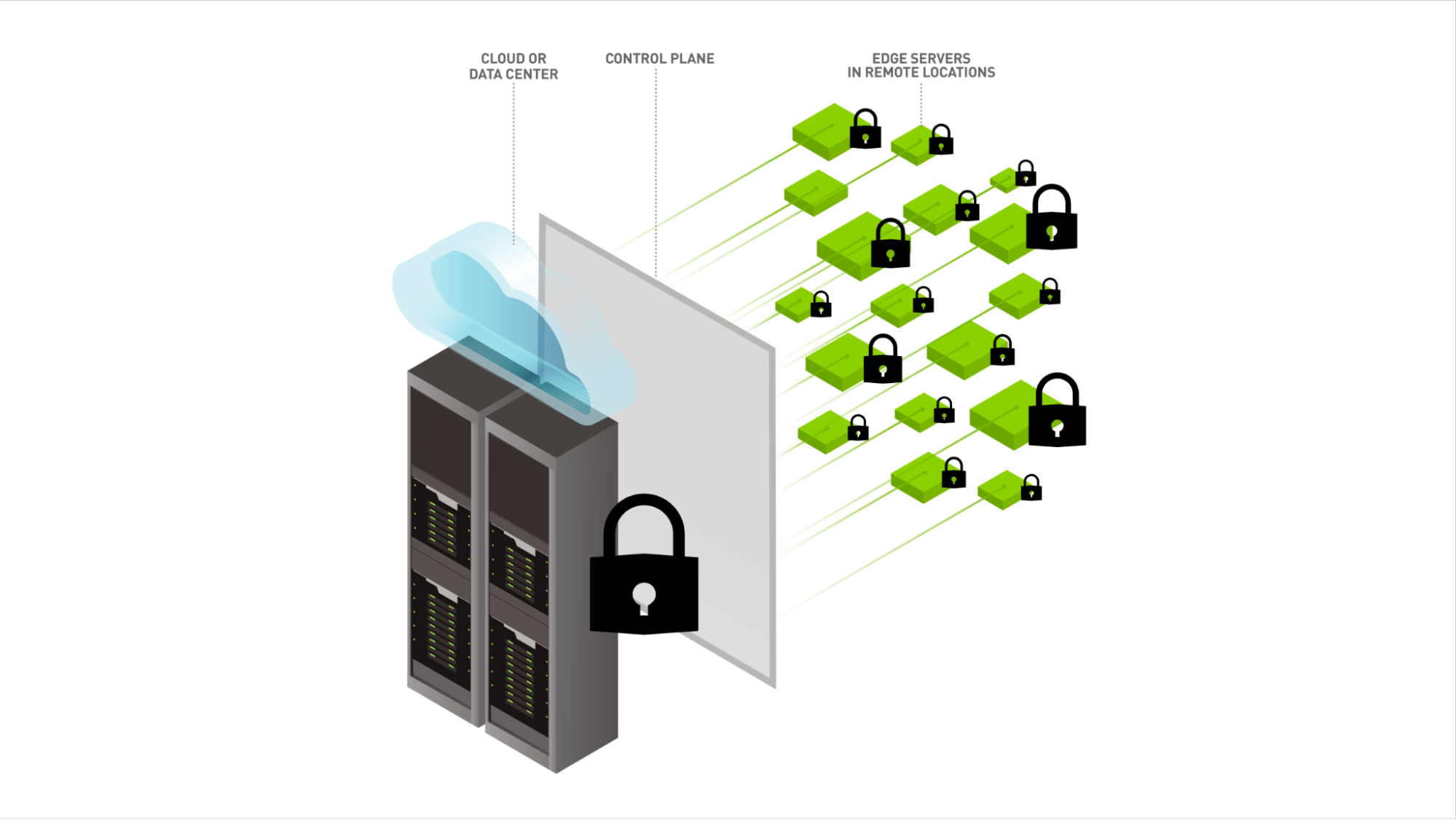
Edge computing, with its distributed nature and reliance on numerous endpoints, presents a unique security landscape. Unlike traditional centralized systems, edge computing involves processing data closer to the source, raising concerns about securing a multitude of entry points. As devices become part of the edge ecosystem, the attack surface expands, necessitating a comprehensive approach to mitigate potential threats.
Challenges in Edge Computing Security
One of the foremost challenges in edge computing security is the sheer diversity of devices and endpoints connected to the network. Ranging from IoT devices and sensors to gateways and servers, each component introduces a potential vulnerability. Securing this diverse ecosystem demands solutions that can adapt to varying device capabilities while ensuring a cohesive and effective defense strategy.
Data Encryption and Privacy at the Edge
The decentralized nature of edge computing often involves transmitting sensitive data across networks. To protect this data from unauthorized access, encryption plays a pivotal role. Implementing robust encryption protocols ensures that data remains secure in transit and at rest. Additionally, privacy considerations become paramount, as edge computing applications may involve processing personal or sensitive information closer to the source.
Zero Trust Security Model for Edge Devices
Adopting a Zero Trust security model is essential for edge computing environments. Unlike traditional perimeter-based security, Zero Trust assumes that no device or user is inherently trustworthy, requiring continuous authentication and verification. This approach becomes particularly crucial in edge computing, where devices dynamically connect and disconnect from the network, necessitating a proactive security stance.
Edge Device Authentication and Access Control
Securing edge devices starts with robust authentication mechanisms. Implementing strong, multi-factor authentication ensures that only authorized entities can access the edge infrastructure. Additionally, granular access controls help restrict privileges based on user roles and responsibilities, minimizing the potential impact of a security breach.
Real-Time Threat Detection and Response
The dynamic nature of edge computing demands real-time threat detection and response capabilities. Traditional security measures that rely on periodic scans and updates may not suffice. Edge computing security solutions should employ continuous monitoring, behavior analytics, and artificial intelligence to identify anomalies and potential threats in real time, enabling swift and targeted responses.
Ensuring Physical Security at Edge Locations
While cybersecurity measures are crucial, physical security at edge locations is equally important. Edge devices deployed in remote or exposed locations are susceptible to physical tampering or theft. Implementing measures such as secure enclosures, surveillance, and environmental controls adds an additional layer of protection, ensuring the integrity of the edge infrastructure.
Collaborative Security Efforts in Edge Ecosystems
Securing edge computing environments is not a solitary endeavor. Collaboration among stakeholders, including device manufacturers, service providers, and cybersecurity experts, is paramount. Establishing industry-wide standards and best practices for edge computing security contributes to a more resilient and secure ecosystem, fostering trust among users and organizations.
Future Trends in Edge Computing Security
As edge computing continues to evolve, so do the security paradigms associated with it. Future trends in edge computing security include the integration of Artificial Intelligence (AI) for predictive threat analysis, the development of specialized security solutions for edge devices, and increased emphasis on decentralized identity management. Staying ahead of these trends is essential for organizations to proactively address emerging security challenges.
Exploring Comprehensive Edge Computing Security Solutions
For those seeking comprehensive insights and solutions for edge computing security, consider exploring Edge Computing Security. This dedicated resource provides valuable information on the latest trends, best practices, and technologies to fortify edge computing environments against evolving cybersecurity threats. As businesses increasingly rely on edge computing for agility and efficiency, prioritizing security measures ensures a resilient and protected digital landscape.
