Securing IoT: Essential Practices in Programming
The proliferation of Internet of Things (IoT) devices has brought unprecedented connectivity, but it also raises significant security concerns. In the realm of programming for IoT, ensuring robust security measures is paramount. Let’s delve into essential practices for securing IoT through effective programming.
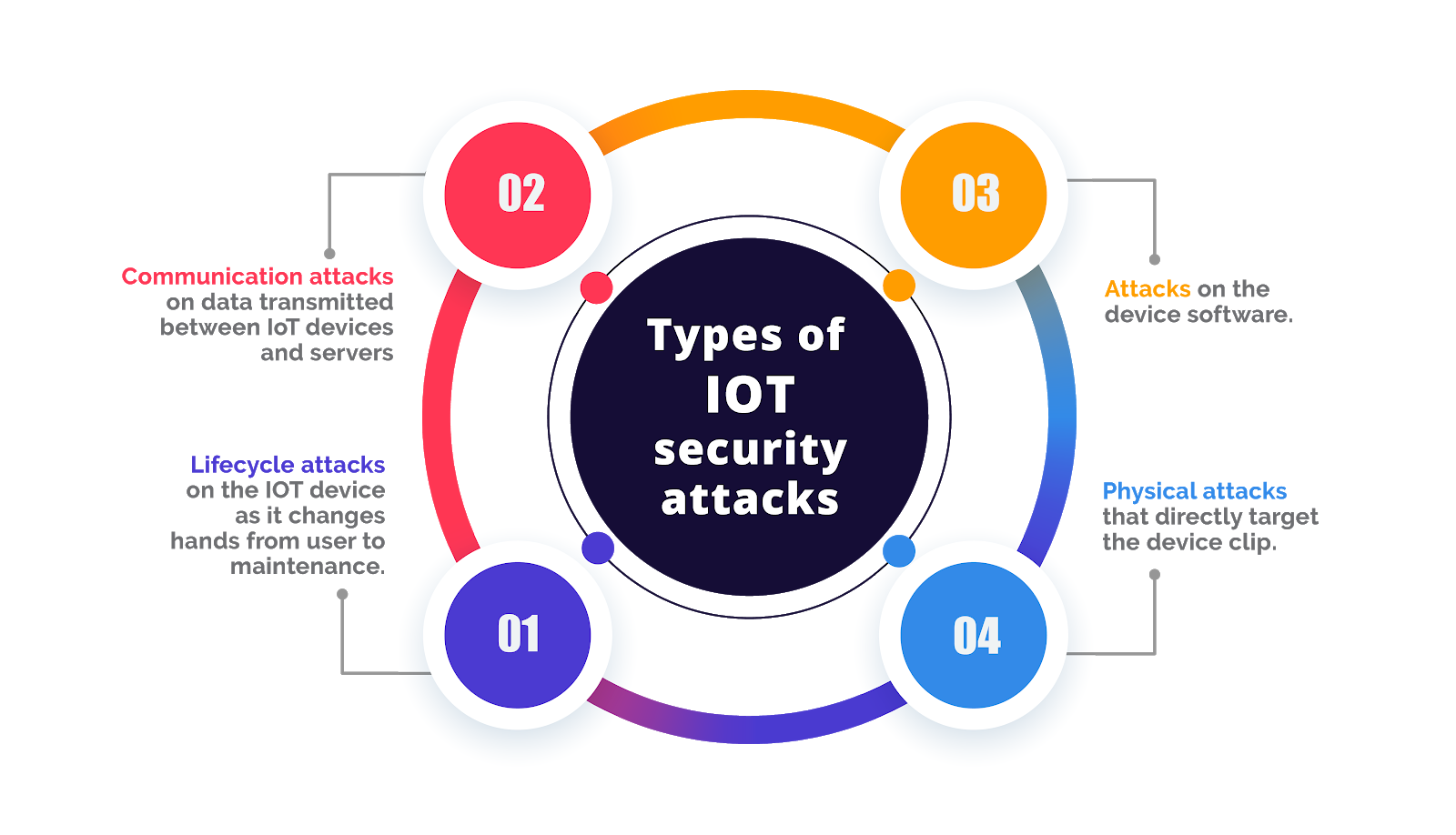
Understanding IoT Security Challenges
Programming for IoT involves addressing unique security challenges. With a vast network of interconnected devices, each potentially vulnerable to cyber threats, programmers must understand the specific risks associated with IoT deployments. This understanding forms the basis for implementing effective security measures.
Now, if you’re eager to fortify your knowledge about IoT security in programming, consider exploring IoT security in programming for in-depth resources and insights tailored to enhance your skills in securing IoT devices.
Authentication and Authorization Protocols
Implementing robust authentication and authorization protocols is fundamental in securing IoT devices. Through programming, developers establish secure access controls, ensuring that only authorized entities can interact with the devices. This involves employing secure authentication mechanisms such as OAuth or token-based systems.
Data Encryption for Confidentiality
IoT devices often handle sensitive data, making encryption a crucial aspect of programming for security. Through coding, data exchanged between devices and the central systems can be encrypted, safeguarding it from interception by malicious actors. Implementing strong encryption algorithms ensures the confidentiality of information.
Secure Device Lifecycle Management
Effective programming for IoT security involves managing the entire lifecycle of devices securely. This includes secure device onboarding, updates, and decommissioning. Programmers must ensure that devices are shipped with secure configurations, receive timely security updates, and are decommissioned in a manner that eliminates potential security loopholes.
Network Security Measures
IoT devices communicate through networks, making network security a vital consideration in programming. Implementing secure communication protocols, such as TLS/SSL, helps protect data in transit. Additionally, programmers must configure firewalls, intrusion detection systems, and regularly monitor network traffic to identify and mitigate potential threats.
Implementing Device Firmware Security
The firmware running on IoT devices is a critical element that demands attention in programming for security. Ensuring secure coding practices, conducting regular security audits, and signing firmware updates with cryptographic signatures are essential steps to prevent unauthorized modifications and protect the integrity of device firmware.
Security by Design Principle
A proactive approach to IoT security involves adhering to the security by design principle during the programming phase. By integrating security considerations into the initial design and development stages, programmers can create robust and resilient IoT systems that are inherently secure, minimizing the need for reactive measures.
User Education and Access Controls
Even the most secure IoT systems can be vulnerable if users are not adequately informed and educated. Through programming, developers can implement user-friendly interfaces that provide clear information about security practices. Additionally, access controls must be programmed to restrict user privileges and prevent unauthorized actions.
Regular Security Audits and Updates
Programming for IoT security is an ongoing process that requires regular audits and updates. Conducting security audits helps identify vulnerabilities and weaknesses in the system. Programmers must stay vigilant, promptly address identified issues, and ensure that devices receive regular security updates to stay resilient against evolving threats.
Collaboration with Security Experts
Given the complexity of IoT security, programmers should collaborate with cybersecurity experts. This partnership ensures a comprehensive approach to security, leveraging the expertise of professionals who specialize in identifying and mitigating advanced threats. Collaboration contributes to the development of robust security strategies.
Conclusion
In conclusion, securing IoT through effective programming is a multifaceted endeavor that demands a proactive approach. From implementing authentication protocols to securing firmware and conducting regular audits, programmers play a pivotal role in fortifying IoT devices against potential threats. If you’re committed to mastering IoT security in programming, explore IoT security in programming for resources and insights tailored to enhance your skills in this critical field.
